Introduction
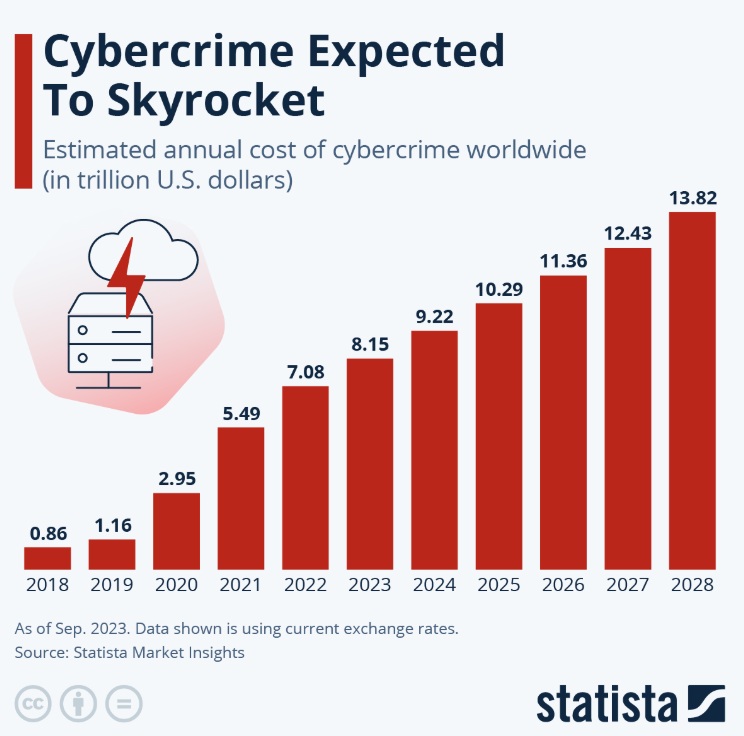
Technological advancements have raised cybersecurity issues, compelling businesses to integrate advanced risk management strategies to combat cyber threats. In the last few years, the prevalence of cyber crimes has significantly increased, making it a plaguing issue for businesses and customers. A Statista report shows that around 46% of global enterprises pay ransom after a ransomware attack. The total cost of cybercrimes was $9.22 trillion globally in 2024 and is predicted to skyrocket to $13.82 trillion by 2028.
(Source: Statista, 2024)
With such an alarming number in view, enterprises are optimizing their risk management strategies and IT security infrastructure to deal with cyber threats. Organizations falling behind in adapting effective security frameworks will not only lose money but also lose out on their competitors. A strong cyber risk management plan can be a savior for businesses to safeguard themselves from such threats.
Cybersecurity Risk Management: What it is and How it Works?
Cybersecurity risk management is an ongoing process encompassing threat identification, analysis, evaluation, and addressing. Managing cybersecurity is a holistic approach in which risk management includes everyone working in an organization. A comprehensive cyber risk management plan clearly states cybersecurity objectives, strategies, frameworks, and practices, along with owners and their responsibilities toward risk management.
At the initial stage of this strategic and systematic risk management process, cyber risks are identified first. This is executed through asset inventory, analyzing existing security controls for loopholes, and identifying potential attack entry points. Following the risk identification process, risks are analyzed to determine their impacts and prioritize them depending on their severity.
Later, risks are mitigated through suitable defense mechanisms, security protocols, and other risk mitigation processes. Through continuous monitoring, real-time threats are detected, the performance of security measures is tracked, and vulnerability tracing is carried out for efficacious cyber risk management.
4 Best Cybersecurity Risk Management Strategies
As we step into 2025, advancements in cybersecurity are now a must for every organization. Rather than mitigating a threat attack, businesses are making their operations security-proof to be prepared beforehand. From threat anticipation to springing back from the setback, a robust cyber risk management strategy must have all the necessary measures to mitigate cyberattacks. Let us have a look at the four best cybersecurity risk management strategies that go beyond just risk mitigation-
-
Zero-Trust Strategies
Zero-trust strategies are built on the principle of ‘never trust, always verify’ to minimize the potentiality of cyber threats and their impacts. This principle assumes the occurrence of a risk beforehand and as an effective measure, promotes strong identity management, micro-segmentation, and limited access to confidential information.
With a rise in remote working, cloud adaptations, and leveraging of AI tools, user impersonation has become a common phenomenon. Impersonating an identity, cyber attackers can plan a malware attack easily. Having a zero-trust architecture can enable organizations to deploy effective zero-trust strategies.
As per another Statista report, over 30% of organizational participants have confirmed their adoption of the zero trust strategy, and 27% have a plan to implement it in 2024. These statistics reveal the effectiveness of this strategy in securing organizational data and assets from unauthorized access. Relying on this ‘don’t trust and verify’ principle, organizations minimize cyber threats through automated threat measures.
Zero-trust strategies can be implemented by building a detailed asset inventory, through which organizations can track users and their accessibility to particular datasets. This helps in deploying a least-privilege access model to limit accessibility to authorized users only.
By moving forward, context-aware controls can be unlocked to determine where the users are, what devices they are on, and their data usage pattern. Coupling this with automated incident response allows systems to automatically revoke access once they detect any suspicious activity.
-
AI for Real-time Threat Identification
Artificial intelligence applications, being the cornerstone of global business operations, are widely explored by businesses for several purposes. In the realm of cybersecurity, businesses are also leveraging the power of AI to boost vulnerability management. AI can parse through system logs, spot real-time threats, and often autonomously respond to minor attacks quite effectively.
-
Risk-Aware Culture
Cyber risk management doesn’t only involve implementing effective risk management measures; it also requires a well-aware workforce who have knowledge about cyber threats and the necessity for them to take action in collaboration with the security team. Through risk-awareness sessions and training, organizations must make the employees threat-ready.
-
Risk-Registering
A risk register is a tool that organizations use to identify and measure the impact of potential risks by giving them scores. In a risk-matrix threat, the score ranges from 0-5 and sometimes 0-10. It helps businesses prioritize the risks depending on the score. Risk score is determined by multiplying risk likelihood with impact. The higher the score, the more impact it is likely to have on the organization. Through this risk evaluation, contingency plans are curated as per individual risks. In the case of cyber security, this risk scoring helps in deploying required risk management strategies.
Conclusion
While talking about cyber risk management, this article has shed light on the best cybersecurity risk management strategies that are effective in minimizing cyber threats. We, at The CEO Views, understand the severity of such attacks and encourage businesses to implement these strategies to effectively overrule cyber attacks.